Go-to Microsoft partner for requirements management since 2015

The Modern Requirements Blog
Featured Articles
Top Blogs
Press Releases
Featured Articles
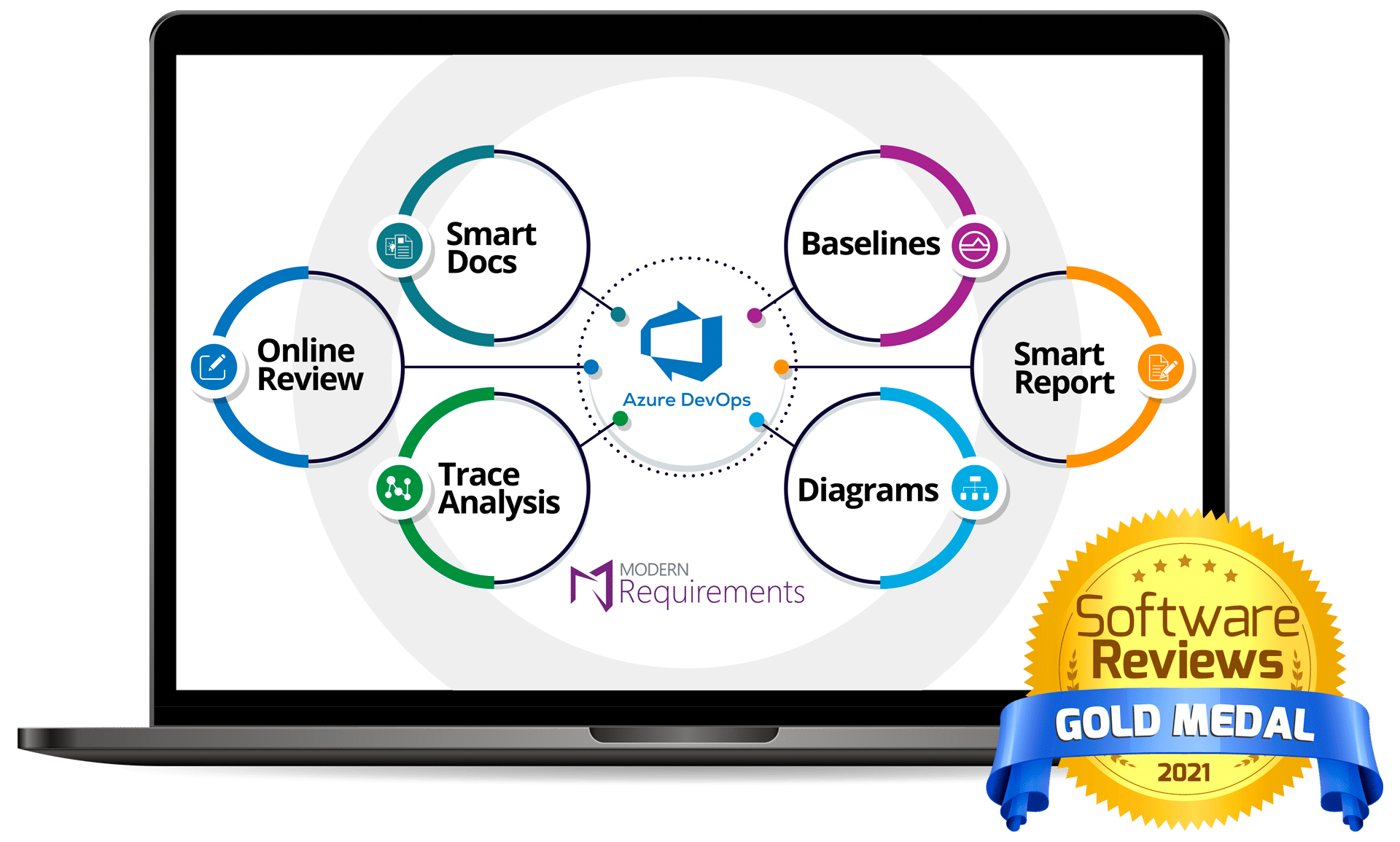
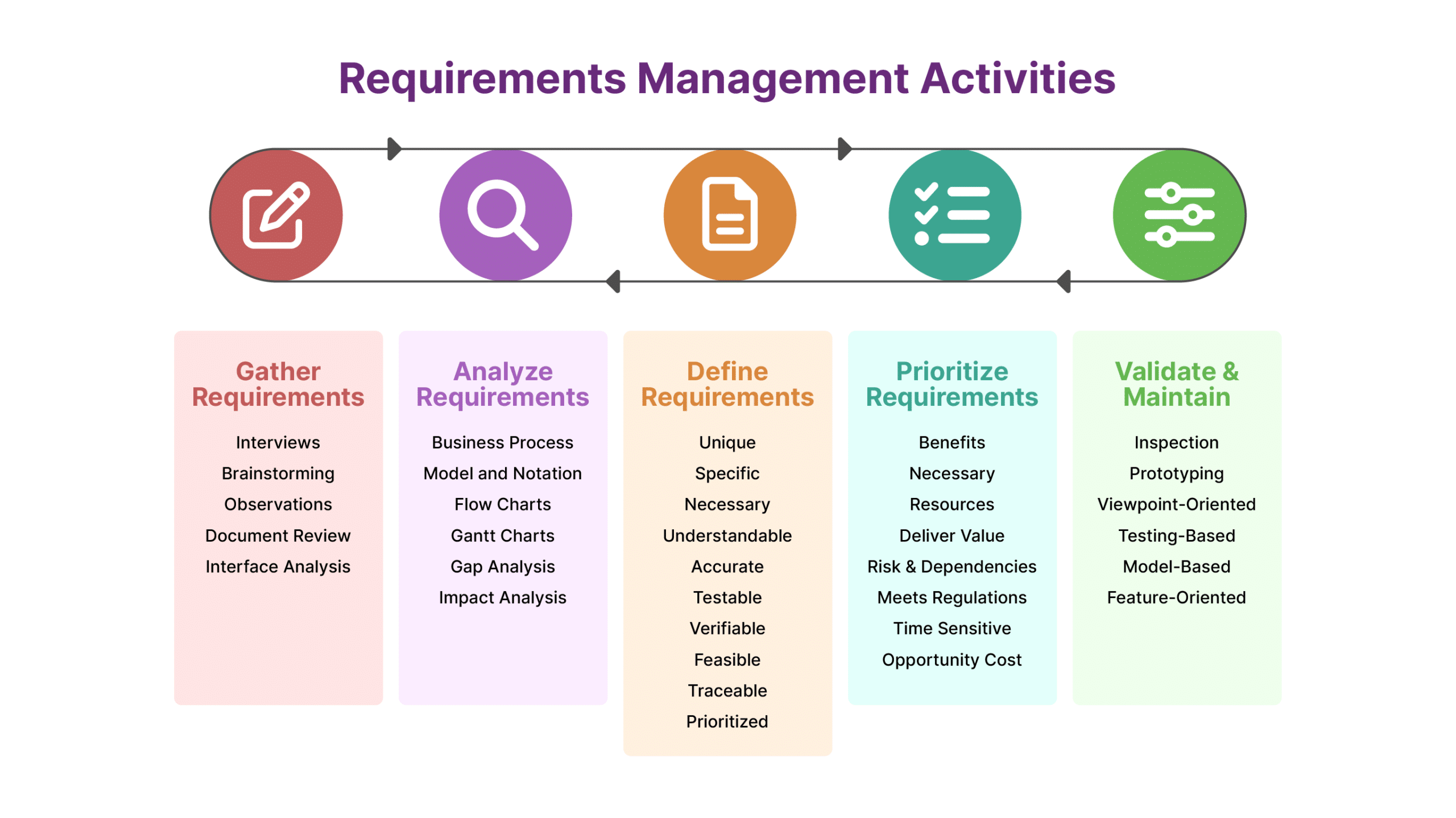
Rely on award-winning solution to power your project & requirements lifecycle in Azure DevOps
Modern Requirements is the only requirements management solution built directly in Azure DevOps and a gold medalist named by independent IT research firms.
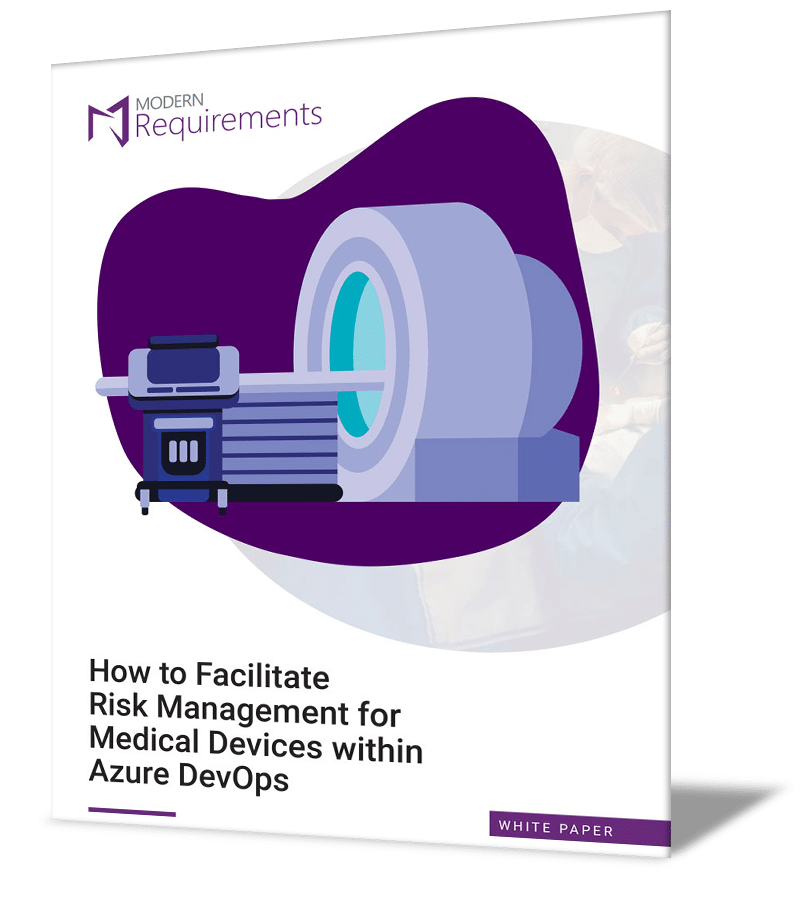
Whitepaper: How to Facilitate Risk Management for Medical Devices within Azure DevOps
In this whitepaper, we will describe how to facilitate risk management for medical devices directly in Azure DevOps. We will focus on how manufacturers can achieve ISO 14971 compliance and overcome key challenges in the process.
Modern Requirements4DevOps
Deep Dive Webinars
Support Articles
All Blogs
See our features in a technical walkthough with product experts.

Reduce UAT Efforts
50% Reduction in UAT efforts

Proven Time Saving
80% time saving on creating Trace Analysis

Streamline Approvals
Significant reduction in approval delays

Increase Performance
50% requirements productivity improvement

Reduce Rework
10-fold reduction in development rework
Simplify Compliance
40% reduction in compliance reporting efforts
Request a Demo!
- Schedule a demo with one of our trained product experts.
- Receive a personalized demo that mimics your team's process
- Engage our experts on topics such as workflow or best practices.